Implementing Zero Trust Security with Cloudflare
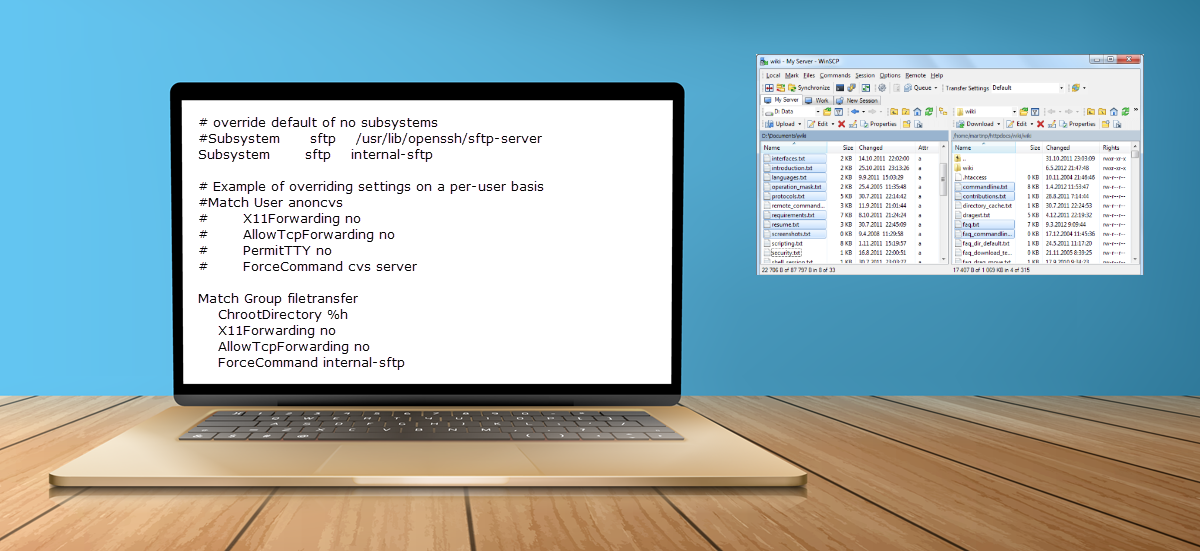
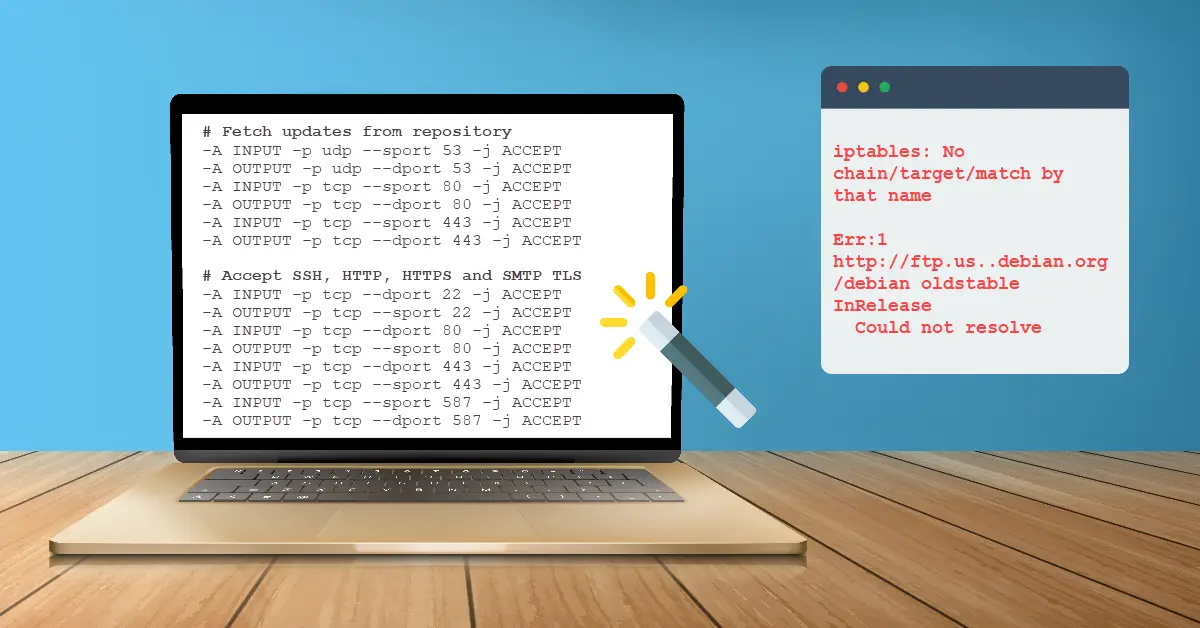
Introduction Any web application that is important to you can be secured by adding 2FA in addition to the standard login username and password. To hide the app's vulnerabilities, one could restrict access with Nginx HTTP basic authentication, which will…