Introduction
TrueCrypt is the first on-the-fly encryption (OTFE) that I used and when it got discontinued, I switched to VeraCrypt. Similar to TrueCrypt, VeraCrypt is a small encryption software that is used for OTFE and is a fork of the discontinued TrueCrypt project. One can create an encrypted file container, encrypt a non-system partition/ drive and encrypt the system partition or entire system drive. It is extremely configurable, providing many options when we use the volume creation wizard, for example, standard or hidden volume, filesystem type and encryption algorithm etc. And best of all, it’s absolutely free and is still maintained!
Background
I would always save all my web projects in my USB flash drive and bring it to office and back home daily to continue my web development. All my hard work, the entire public_html folder, config.php file for my e-commerce web store which stores the MySQL database credentials including the database backups are kept in the flash drive. I thought to myself, what if I lose the USB? For me, the data is more precious than the thumb drive itself because anyone who picks it up will know the credentials to my database. Although remote MySQL access is disabled by default on Linux but I had phpMyAdmin online and the stranger will be able log in with the found credentials!
So, what are the chances of one losing a flash drive? I had changed a few flash drives over the last 10 years due to hardware failure and I had lost it once when I attended a mid-night class and left it plugged in to the lab computer. The lab is primarily used by students from the Computer Engineering course so one can imagine the danger and the high possibility of having one of them picking up my USB. While I feel disappointed at losing but at the same time, I felt lucky and safe that whoever picks it up will have no access to my confidential files because they are stored in a encrypted volume.
Step 1 – Download VeraCrypt
Download the portable version from VeraCrypt website. Run the downloaded file to unzip into the thumb drive because we need to run VeraCrypt.exe to mount and demount the encrypted volume. The entire folder is less than 60 MB and these days, the average USB size is at least 32 GB.
Step 2 – Volume Creation Wizard
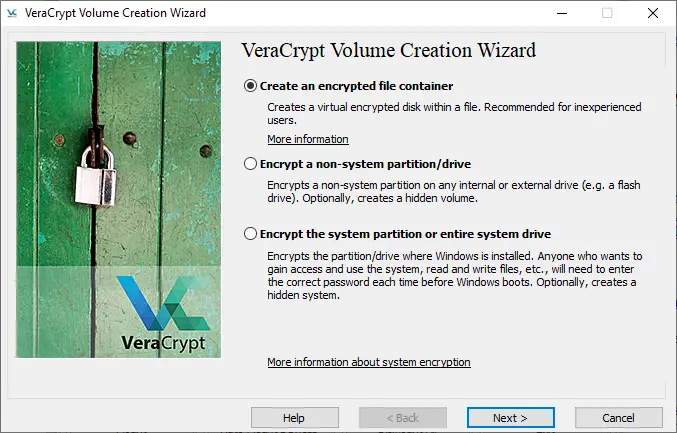
- Run VeraCrypt.exe
- Volumes > Create New Volume
- Create an encrypted file container
- Standard VeraCrypt volume
- Select File > Browse to the root of USB and give a generic file name such as helloword.txt (we can omit .txt as it is not required as such file extension is purely decorative)
- Encryption Algorithm: AES | Hash Algorithm: SHA-512
- Volume size is up to individual. In my case, I set aside 20 GB for the encrypted volume and remaining 10 GB as ‘normal’ usable space for a 32 GB flash drive.
- Enter a complex password and uncheck all options.
- Volume Format: NTFS (working on Windows) or exFAT (working on Linux)
- Format
Questions? Answers!
3. Why not encrypt the entire thumb drive?
Yes, you can. The reason for me choosing to encrypt a portion of the USB is so that I can use the remaining space just like any others non-encrypted flash drives. There are times which I had to use it to transfer files between two systems. Thus, the main reason is convenience as I don’t have to mount and show anyone that I am using an encrypted drive.
4. Why not hide the encrypted volume?
The text goes like this, “It may happen that you are forced by somebody to reveal the password to an encrypted volume… Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume”. In my opinion, this has been greatly exaggerated and having an AES encrypted volume is already more secure than the average USB user hence I feel there isn’t a need to hide. It is also easier to see and remember the encrypted volume presence.
6. Why use AES encryption with SHA-512 hash?
While I have not studied the difference on other algorithms such as Serpent or Twofish but I know that AES is commonly deployed in our everyday life, for example, our WiFi SSID password encryption as WPA2-AES. I just felt that setting a complex hard-to-guess password is more important.
9. NTFS or exFAT?
I had chosen NTFS because I work with Windows at home and in office. While both have their pros and cons in terms of read write speed, NTFS has one distinct advantage which is the journaling file system. It means that in addition to writing information to the disk, the file system also maintains a log of all changes made. This feature makes NTFS particularly robust when it comes to recovering from various kinds of failures, such as a power loss or a system crash. There are many times that I had pull out my USB without properly dismounting the encrypted volume and so far, I have not lost any data or damage the filesystem.
Step 3 – Write Mount and Dismount Batch Files
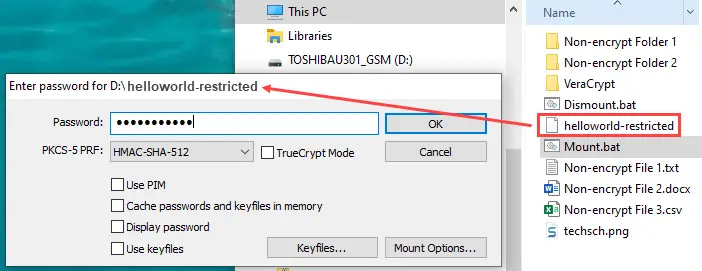
We can mount the encrypted volume by running VeraCrypt.exe on the portable USB. Select the encrypted volume, then go to Volumes > Mount Volume. Enter the password and you can access the secret files from the assigned drive. To dismount, we run VeraCrypt.exe again and click the Dismount All button. We can however write Windows batch files to quickly mount and dismount the designated encrypted volume.
VeraCrypt\veracrypt /v gat-x103 /l x /e /b /hash sha512 /qOpen a new file in Notepad or any text editor and input above code and save it as mount.bat. Do the same for below code and save it as dismount.bat. We can now double-click these files to mount and dismount easily.
VeraCrypt\veracrypt /q /d xCommand line usage on VeraCrypt can be found here.
- /v is the name of the encrypted volume.
- /l is the drive letter to mount the volume as.
- /e to open the mounted volume in File Explorer on success mount.
- /b to beep after a volume is mounted successfully.
- /hash to specify the hash algorithm to use.
- /q to quickly mount or dismount volume without opening VeraCrypt window.
- /d is to dismount a volume by drive letter.
Conclusion
BitLocker To Go in Windows 10 is another software to encrypt removable data drives. All these tools help to protect our data in the event we lose our flash drive and it falls into the wrong hands. While it is morally wrong to access someone else thumb drive without permission, the person might be doing it out of curiosity. Also, as flash drives get smaller in physical size, it is very easy for us to misplace them. Therefore, I would definitely recommend VeraCrypt for its ease of use and portability, e.g. no need for local installation and the volume creation wizard which has various options and encryption algorithms to choose from.