Introduction
You may want to use one of your existing servers as a SFTP server without subscribing to another EC2 instance. Or you would like to have multiple SFTP users/vendors on a single SFTP server to save on resources and ease of maintenance. In these two scenarios, you will not want the external SFTP users to see or mingle with your server ‘root’ files or browse other user’s home directory. Therefore, one way is to set up chroot jail for each user to their home directory.
Prerequisites
- Tutorial is based on Ubuntu 18.04.6 LTS but should work for most Linux distributions
- root access because need to edit sshd_config
Step 1 – Edit /etc/ssh/sshd_config
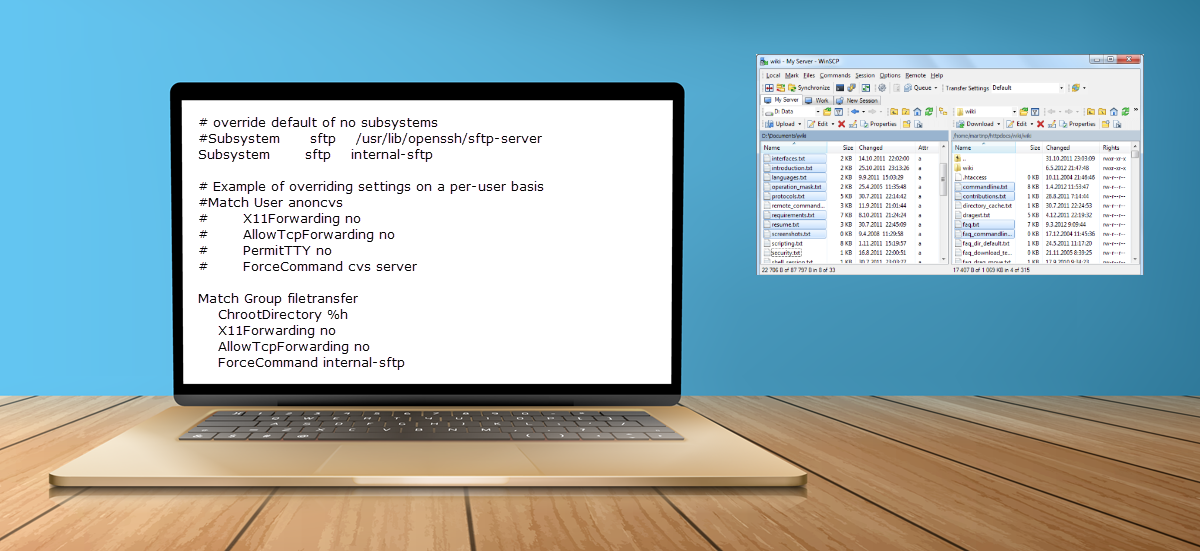
Both sftp-server and internal-sftp are port of OpenSSH. The subsystem internal-sftp simply bind a different file system root on users. Next, add a Match Group section at the bottom where %h is replaced by the path of user home directory (e.g., /home/username). This will add a group for jailed SFTP users, which we will assign in the next step.
# override default of no subsystems
#Subsystem sftp /usr/lib/openssh/sftp-server
Subsystem sftp internal-sftp
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
Match Group filetransfer
ChrootDirectory %h
X11Forwarding no
AllowTcpForwarding no
ForceCommand internal-sftpStep 2 – Change User and Group Ownership of home directory
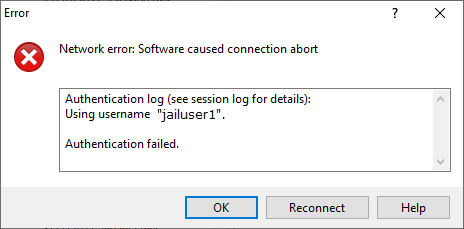
Use the chown command to put the Linux users into the chroot jail group (filetransfer). User ownership must change to root:filetransfer or else /var/log/auth.log: fatal: bad ownership or modes for chroot directory “/home/jailuser1”. Likewise, an FTP client like WinSCP will abort the connection with “Authentication failed.” error message.
$ chown root:filetransfer /home/jailuser1
$ chown root:filetransfer /home/jailuser2
$ ls -l
drwxr-xr-x 7 standarduser standarduser 4096 Jul 27 16:24 standarduser
drwxr-xr-x 5 root filetransfer 4096 Jun 27 09:47 jailuser1
drwxr-xr-x 6 root filetransfer 4096 Dec 21 2021 jailuser2Step 3 – Change User and Group Ownership of Subdirectories
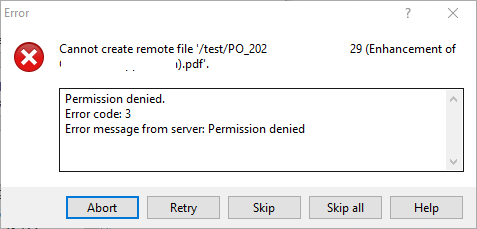
If you connect with WinSCP after Step 2, you will notice that the user is now unable to browse outside his home directory. However, we will encounter “Permission denied” error if we try to upload a sample file to user home directory. To get around this, we create subdirectories (e.g., uploads) in /home/user and update ownership to username:filetransfer or else WinSCP will throw an “Error message from server: Permission denied” error message again if we try to upload a sample file to the subdirectory.
$ ls -l /home/jailuser1
drwxr-xr-x 2 jailuser1 filetransfer 4096 Dec 21 2021 Downloads
drwxr-xr-x 2 jailuser1 filetransfer 4096 Jun 27 09:29 UploadsConclusion
A SFTP chroot jail allows the server administrator to create a secure directory that confines the SFTP users to specific subdirectories. Therefore, we can easily isolate users from one another and prevent them from browsing the file system. This will work with non-standard SFTP ports such as 2222 and 15722.